Gefragt von: Dane Sullivan
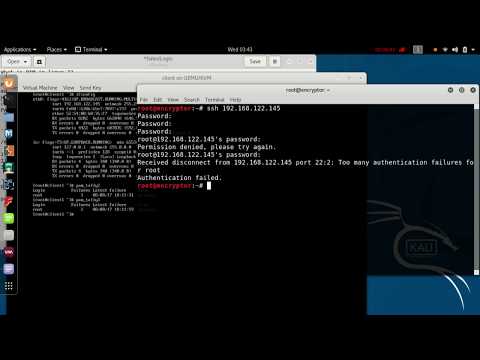
Fragesteller AllgemeinesSsh2 Login Attempt Vulnerability
Der Link der Ssh2 Login Attempt Vulnerability-Seite ist unten angegeben. Seiten, die sich auf Ssh2 Login Attempt Vulnerability beziehen, werden ebenfalls aufgelistet.
Zuletzt aktualisiert: 2021-04-19
Befolgen Sie diese einfachen Schritte:
- Schritt 1. Gehen Sie über den offiziellen Link unten zur Seite Ssh2 Login Attempt Vulnerability.
- Schritt 2. Melden Sie sich mit Ihrem Benutzernamen und Passwort an. Der Anmeldebildschirm wird nach erfolgreicher Anmeldung angezeigt.

 US
US UNKNOWN
UNKNOWN IN
IN